You consider taking the Cisco 350-201 (CBRCOR) exam, but find it difficult to do so in such a short period of time. You’re not really ready to take the exam yet, so you’re trying to find out more about the exam, like 350-201 CBRCOR Braindumps or anything that can help you. Then I tell you, you’ve come to the right place. This blog is designed to help you pass the Performance CyberOps Using Cisco Security Technologies (CBRCOR) exam. The best way to learn is to practice. Practice a lot of Cisco 350-201 exam questions. You can get it with the help of 350-201 cbrcor dumps pdf.

Get it now: https://www.pass4itsure.com/350-201.html 350-201 cbrcor dumps (PDF +VCE)
Updated 350-201 CBRCOR Dumps Pdf 2022 [FREE]
[google drive] 350-201 exam pdf https://drive.google.com/file/d/1nUIzMwqvRZmh8Vdd7OrtSLM9k1STrc8j/view?usp=sharing
Real Valid 350-201 Exam Questions Test
QUESTION 1
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having
the names of the 3 destination countries and the user\\’s working hours, what must the analyst do next to detect an
abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
Correct Answer: D
QUESTION 2
An organization installed a new application server for IP phones. An automated process fetched user credentials from
the Active Directory server, and the application will have access to on-premises and cloud services. Which security
threat should be mitigated first?
A. aligning access control policies
B. exfiltration during data transfer
C. attack using default accounts
D. data exposure from backups
Correct Answer: B
QUESTION 3
DRAG DROP
Drag and drop the NIST incident response process steps from the left onto the actions that occur in the steps on the
right.
Select and Place:
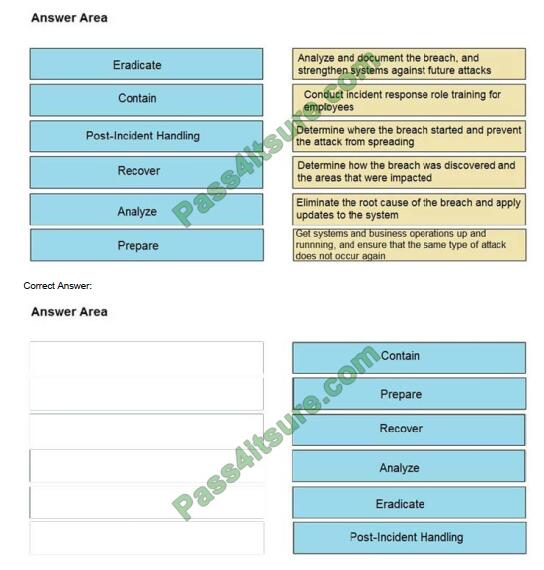
Reference: https://www.securitymetrics.com/blog/6-phases-incident-response-plan
QUESTION 4
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a
conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site
through which the employee downloaded a PDF attachment infected with ransomware.
The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server.
Which security solution is needed at this stage to mitigate the attack?
A. web security solution
B. email security solution
C. endpoint security solution
D. network security solution
Correct Answer: D
QUESTION 5
What is the HTTP response code when the REST API information requested by the authenticated user cannot be
found?
A. 401
B. 402
C. 403
D. 404
E. 405
Correct Answer: A
QUESTION 6
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
A. Classify the criticality of the information, research the attacker\\’s motives, and identify missing patches
B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation
plan
Correct Answer: B
QUESTION 7
DRAG-DROP
Drag and drop the type of attacks from the left onto the cyber kill chain stages at which the attacks are seen on the
right.
Select and Place:
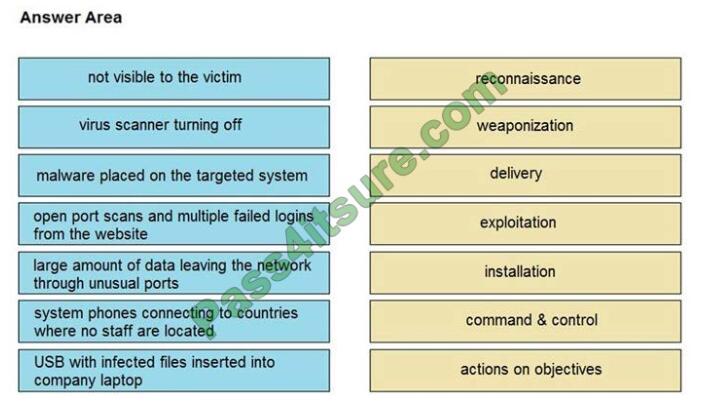
Correct Answer:
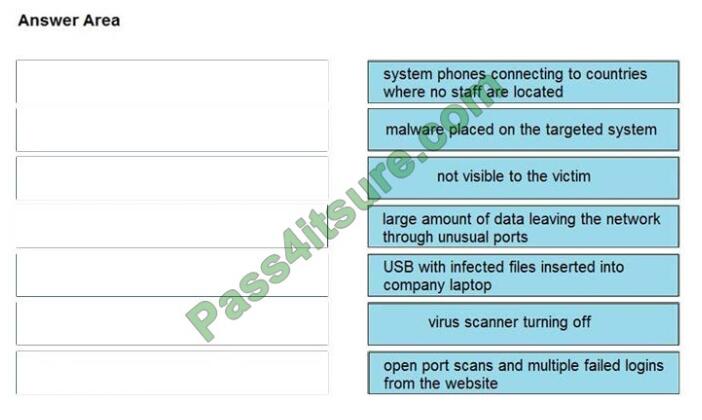
QUESTION 8
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a
crafted packet to a device resets the credentials, makes the device unavailable, and allows a default administrator
account login.
Which step should an engineer take after receiving this alert?
A. Initiate a triage meeting to acknowledge the vulnerability and its potential impact
B. Determine company usage of the affected products
C. Search for a patch to install from the vendor
D. Implement restrictions within the VoIP VLANs
Correct Answer: C
QUESTION 9

Refer to the exhibit. What results from this script?
A. Seeds for existing domains are checked
B. A search is conducted for additional seeds
C. Domains are compared to seed rules
D. A list of domains as seeds is blocked
Correct Answer: B
QUESTION 10

Refer to the exhibit. An engineer is performing a static analysis on malware and knows that it is capturing keys and
webcam events on a company server. What is the indicator of compromise?
A. The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard
manufacturer, and connected removable storage.
B. The malware is ransomware querying for installed anti-virus products and operating systems to encrypt and render
unreadable until payment is made for file decryption.
C. The malware has moved to harvest cookies and stored account information from major browsers and configuring
a reverse proxy for intercepting network activity.
D. The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of
loggers and webcam capture in locally encrypted files for retrieval.
Correct Answer: B
QUESTION 11
The incident response team was notified of detected malware. The team identified the infected hosts, removed the
malware restored the functionality and data of infected systems and planned a company meeting to improve the
incident handling capability.
Which step was missed according to the NIST incident handling guide?
A. Contain the malware
B. Install IPS software
C. Determine the escalation path
D. Perform vulnerability assessment
Correct Answer: D
QUESTION 12
Refer to the exhibit. What is occurring in this packet capture?
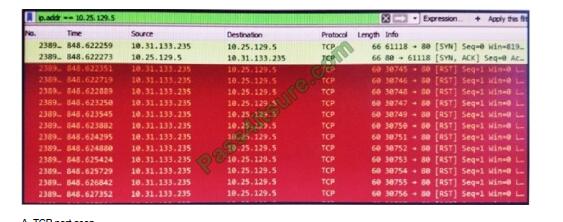
A. TCP port scan
B. TCP flood
C. DNS flood
D. DNS tunneling
Correct Answer: B
QUESTION 13
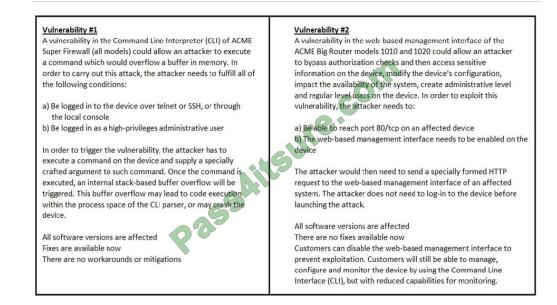
Refer to the exhibit. How must these advisories be prioritized for handling?
A. The highest priority for handling depends on the type of institution deploying the devices
B. Vulnerability #2 is the highest priority for every type of institution
C. Vulnerability #1 and vulnerability #2 have the same priority
D. Vulnerability #1 is the highest priority for every type of institution
Correct Answer: D
QUESTION 14
What is the purpose of hardening systems?
A. to securely configure machines to limit the attack surface
B. to create the logic that triggers alerts when anomalies occur
C. to identify vulnerabilities within an operating system
D. to analyze attacks to identify threat actors and points of entry
Correct Answer: A
QUESTION 15
A company\\’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not
deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An
analyst conducted the risk assessment using the threat sources, events, and vulnerabilities.
Which additional element is needed to calculate the risk?
A. assessment scope
B. event severity and likelihood
C. incident response playbook
D. risk model framework
Correct Answer: D
Does the exam require a lot of practical experience? I answer you in the affirmative, a must. So get the Cisco 350-201 cbrcor dumps pdf for hands-on exercises!
Share the Cisco 350-201 cbrcor dumps pdf link here https://www.pass4itsure.com/350-201.html 100% guaranteed success.
